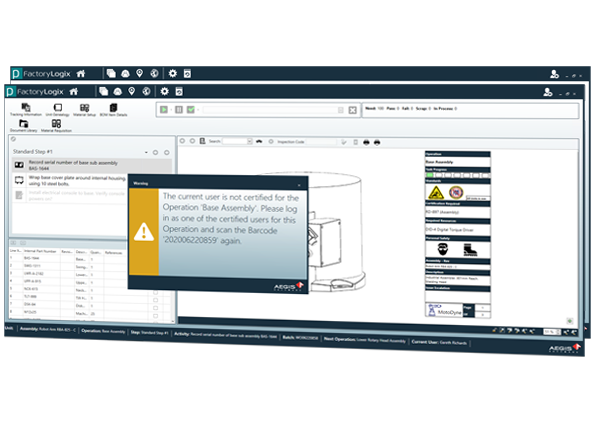
Critical step review
In key business links, how to talk about the data review entrance.

Active Defense Against Attacks
The system is capable of defendingXSS,CSRF,SQLInjection,DDOSAnd other common attacks.

Sensitive data encryption
Sensitive data can be encrypted and stored, and for communication services, sensitive interfaces are also encrypted and transmitted.
Control costs, ensure product quality, and simplify compliance.

Risk reduction

Driving Continuous Improvement

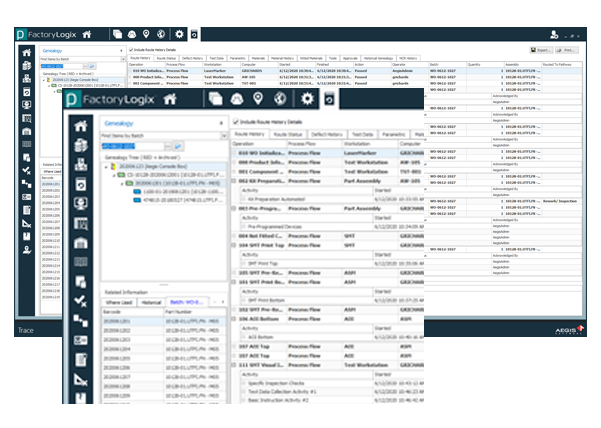
Product production process traceability

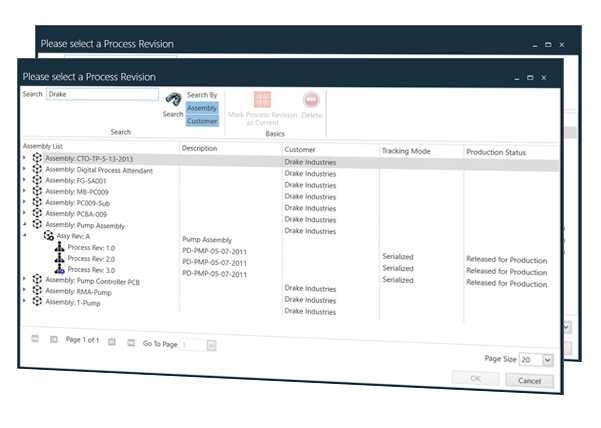
Quick Release Process

The core process is only leaking

Centralization of data management
Other Customers We Helped